Future of Cyber Security
 |
| Future of Cybersecurity |
Future of cyber security. Hello guys in this blog post we going to see about the future of cyber security and different types cyber attacks and the brief history of the cyber security. So Now Let's Start Our Blog post with the introduction of cyber security.
1. Introduction of Cyber Security :
 |
| Future of Cybersecurity |
Future of cyber security so without any further delay let's take a look at today's agenda we'll start this session by understanding why we need cyber security. and what does it do then we shall discuss type of cyber attacks followed by the brief history of cyber security moving ahead i'll be speaking about modern day cyber security system and what the future of cyber security. Understanding why and what is cyber security we live in a digital era that understands that our private information is more wonderable than ever before what i'm trying to say here is we all live in a world that is networked together from internet banking to government infrastructure where data is stored on computers and other devices portion of this data can be a sensitive information for which an any unauthorized access could have a negative consequences.
Why we need Cyber Security?
 |
| Future of Cybersecurity |
So why do we need cyber security i'm sure by now you guys have a wild guess why we need cyber security well with lots of online activities several attacks are on the rise and the cyber attack is now an international concern organizations transmit sensitive data across the network to other device while doing their business activities and cyber security ensures protecting that information and the system that is being used to process or store it. (Future of cyber security)So what is cyber security right well cyber security is a set of principles and practices designed to protect our computer resources and online information against threats what i'm trying to say here is due to our heavy dependency on computer systems in modern industry that store and transmit an abundant amount of confidential and essential information cyber security has become a critical part of every organizations digital function.
2. Different types of cyber attacks :
 |
| Future of Cybersecurity |
I mentioned earlier we live in an era where we are totally dependent on computers and internet for our day-to-day activities what basically happens in cyber attack is the exploitation of computer systems and network and we can broadly classify these types of attacks into two categories,
1. Web-based attacks :
Starting off with web-based attacks these are the attacks that occur on a website or application some of the important web-based attacks are like injection attack in injection attack some data will be injected into web application to manipulate the back-end security and fetch the required information the example for this is sql injection, code injection, log injection and xml injection and many more then we have something called as session hijacking it's the attack on user session over a protected network you see web applications create cookies to store the state and users session by steering the cookies an attacker can have access to all the user data then we have phishing phishing is a type of attack which attempts to steal sensitive information like user login credentials credit card numbers and anything else it occurs when an attacker is masquerading as a trustworthy entity in an electronic community network moving ahead to brute force it is a type of attack which uses trial and error method this attack generates large number of guesses and validates them to obtain actual data like user id passwords and anything else this attack may be used by criminals to crack encrypted data or by security analyst to test an organization's network security.
2. System-based attacks :
So what is system-based attacks right these are the attacks that are intended to compromise a computer or computer network some of the important system-based attacks are like viruses okay. Virus is a type of malicious software program that spreads throughout the computer files without the knowledge of a user wondering how it works well it's a self-replicating malicious computer program by making copies of itself into other computer program when it's executed then (Future of cyber security)we have worms it is a type of malware whose primary function is to replicate itself to spread throughout the computer in general it works the same as a computer virus but worms often generate for email attachment that appear to be trusted senders moving ahead to trojan horse it is a malicious program that causes unexpected changes to computer setting or unusual activity even when the computer should be idle so what happens here is it appears to be a normal application but when opened or executed some malicious code will run in the background without the consent of the user finally we have back doors back door is a method that bypasses normal authentication process a developer may create a back door so that an application or operating system can be accessed for troubleshooting or other purposes.
3. Brief History of Cyber Security :
 |
| Future of Cybersecurity |
So moving ahead in this session let's now look back and see how the field of cyber security evolved over the years. It was in 1972 with the research project on arcnet gave birth to the cyber security where a researcher bob thomas created a computer program called a creeper that would move across the artnet's network leaving a breadcrumb tale wherever it went it read i'm a creeper catch me if you can then ray thompson who is also known as the inventor of an email. Wrote a program called reaper which was able to chase and delete creeper you see reaper was not only the very first program of antivirus software but it was the first self-replicating program making it a first ever computer worm challenging the vulnerabilities of this emerging technology became more and more important as more organizations were starting to use telephone to create remote networks each piece of the connected hardware presented a new entry point and needed to be producted as reliance on computers increase and networking grew it became clear to the government that security has essential and unauthorized access to data and systems could be catastrophic in 1972 to 1974. Witnessed a market increase in discussing around computer security mainly by academic papers creating an early security was undertaken by esd and arcnet with the u.s air force and other organizations that work cooperatively to develop and design security kernel for honeywell computer systems ucla and stanford research institution worked on a similar project in 1980s we all know we moved from arcnet to the internet. (Future of cyber security)The 1980s bought the increase in high profile attacks including those at national css atnt and los alamos national laboratory and also a point that i would like to mention is that it was around the same time when the term trojan horse and computer virus were first used at the time of cold war a threat of cyber espionage evolved in 1985 the u.s department of defense published a trusted computer system. evaluation criteria aka the orange book this provided a guidance on assessing the degree of trust that can be placed in a software that possess certification or census information what security measure manufacture needed to be built into the commercial product then moving on to 1987. the birth of cybersecurity 1987 was the birth year of commercial antivirus the first anti-virus product was for the atari st which saw the release of ultimate virus killer in 1990s world goes online 1990s was quite a year the first polymorphic virus was created british computer magazine pc today released an addition with the free risk that accidentally contained a disk killer virus infecting tens of thousands of computers eicr that is nothing but european institute of computer antivirus research was established around this time then comes 2000's the threads driver c5 and multiply with the internet available in more homes and offices across the globe cyber criminals had moved more devices and software vulnerabilities to exploit there ever before and as more and more data were being kept digitally there was more to plunder in 2001 a new infection technique appeared users no longer needed to download files visiting a infected website was enough to get hacked instead messaging services also began to get attacked and worm designed to propagate via irc that is nothing but internet.
4. Modern day cyber attacks :
 |
| Future of Cybersecurity |
Modern day cyber attacks or in short cyber threats the first step to deal with new array of these threats is to know your enemy that is to know the different types of cyber attacks and malware understanding how they work and how we can protect ourselves and our business and our clients. let's review some of the most common attacks that have thrived last year and expected to grow in the future the
1. Ransomware,
 |
| Future of Cybersecurity |
ransomware example for this is wannacry ransomware is a type of malware that prevents or limits users from accessing their system either by locking the system screen or by locking the user's file until a ransom is paid modern ransomware families are collectively categorized as crypto ransom they encrypt certain files into an infected system and force users to pay the ransom online to get the decryption key ransomware can be downloaded when unsuspecting user visit malicious or compromise website ransomware can also arrive as a payload either dropped or downloaded by other malware some ransomware are known to be delivered as attachment with spammed email download from malicious pages or dropped by experts into a vulnerable system the rise of bitcoin contributes greatly to the increase in popularity of ransomware among hackers.
2. Wiper,
 |
| Future of Cybersecurity |
Then we have wiper the example for this is no pity this type of malware might walk like a ransomware and quack like a ransomware but is a wiper the intention of this malware is to wipe out all your data in contrast to the ransomware that is based on the financial motive of cyber crime the Wiper is focused on causing damage and chaos among its victim it can be caused by government-led group or terror organization as a part of cyber warfare or by ruthless competitors who are willing to go all means including paying hackers to attack their rivals
3. Spyware,
 |
| Future of Cybersecurity |
The next most common type of cyber threat is spyware example for this is keylogger spyware is a malware that is designed to correct information and monitor the activity of computer that they are installed on spyware can collect any information that can benefit the attacker such as password credit card details documents commercial secrets browsing history and many more it can be programmed to perform complicated actions like recording keystrokes or take screenshots whenever you use a certain program some spyware can even activate computers microphone and camera to record everything that is happening in the area around the computer. (Future of cyber security)Spyware can be used to analyze user preference to customize online advertising for those users or even for a harmful course such as identifying theft credit card theft fraud blackmail and industrial espionage usually this kind of malware is developed by professional hackers who then sell the secrets in the black market for the use of online fraud and other illegal activities.
4. Adware,
 |
| Future of Cybersecurity |
Then we have adware and the best example for this is one click downloader the term adware is frequently used to describe a form of malware that pushes advertisements and banner on your screen most users don't want to see ads but adware can be downloaded without the user being aware of it it usually happens when you download free software or add-ons some adware program have functions built in such as analyzing the size you visit to customize ads in this case adware does more than showing advertisements it collects information about you and you aren't even known about it although some adwords don't have malicious intent the execution can be quite intensive at times for example when adware observes your activities without your consent and sends the information to the software's authority generally there are types of adwords that are usually classified as spyware and thread accordingly however some adware also operates legally.
5. Botnets and DDOS,
 |
| Future of Cybersecurity |
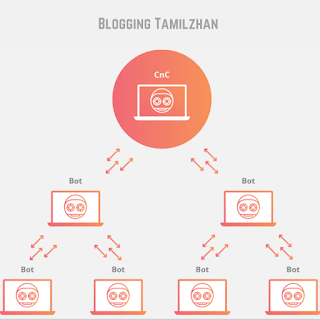
Next one that is nothing but botnets and ddos an example for this is ping of death web robot or simply bought isn't necessarily a bad thing it's a software application that can perform tasks over the internet from web callers to search engines to chat bots to other services the problem starts when a computer serves or other internet device are focused on malware to become the bot network once the device is infected it can be collected remotely by hacker to conduct other attacks other type of botnet attack is distributed denial of service also known as ddos when the infected device generates malicious traffic to make machine or network resource unavailable in many cases users are unaware of botnet infection in the system.
5. Future of Cyber Security :
 |
| Future of Cybersecurity |
So moving ahead let us now see the future of cyber security the rate at which cyber crime is raising is alarming almost every week a new high profile cyber crime is being reported every business no matter what stage of its digital transformation it is it should keep cyber security as its top most priority. (Future of cyber security)let's see know what the future holds right the cyber security professionals are in high demand the need of skilled cyber security professional dires as every passing day new attacks are being coined that are more powerful than the previous ones these rising threats require skilled cybersecurity professionals to help ensure safety for the individuals as well as for the organization we can also expect robust integration of ai in cyber security tools and techniques this is because it can improve expert analyze study and understand cybercrime it can also enhance cybersecurity techniques that company uses to combat cybercriminals and help keep their organizations and customers safe the automation of many roles and tools can also be heavily implemented this will allow performing a constant search for threads and deploy immediate counter measures. I think you could know about the future of cybersecurity. Comment below about my blog.


.png)










1 Comments
serious?? Cloud IT Consultants Madison
ReplyDelete